In today’s digital landscape, a professional business email is more than just a communication tool; it’s a cornerstone of your brand identity. Setting up your business email correctly not only enhances your professionalism but also boosts productivity, streamlining communication with clients and colleagues alike. Imagine sending out emails that carry your brand’s name, reinforcing trust and credibility every time you hit “send.”
This step-by-step guide will walk you through the process of setting up your business email, ensuring that you avoid common pitfalls and maximize efficiency. From selecting the right provider to customizing your inbox, you’ll discover how to create an email setup that meets your unique needs. Whether you’re a startup owner, a freelancer, or part of a larger organization, establishing a professional email account is essential to making a lasting impression. Let’s dive in and elevate your business communication!
Importance of a Professional Business Email
In the fast-paced digital era, the significance of having a professional business email cannot be overstated. It's not just a means of communication; it's a representation of your brand in every correspondence. When clients and partners see an email from a custom domain, it immediately conveys a sense of professionalism and reliability. This first impression can be the difference between being taken seriously or being overlooked in favor of competitors who present themselves more professionally.
Choosing the Right Email Hosting Provider
Selecting the right email hosting provider is a critical step in setting up your business email. The provider you choose will impact the reliability, security, and features available to you and your team. It’s essential to evaluate different providers based on their offerings and how well they align with your business needs. Popular options include Google Workspace and Microsoft 365, each providing unique benefits and features.
Google Workspace, for instance, is known for its user-friendly interface and seamless integration with other Google services like Drive, Calendar, and Meet. This makes it an excellent choice for businesses already using Google’s ecosystem. On the other hand, Microsoft 365 offers robust security features and integration with Microsoft Office applications, making it ideal for companies that rely heavily on tools like Word, Excel, and PowerPoint.
When choosing a provider, consider factors such as storage capacity, ease of use, customer support, and scalability. It's also important to look at the provider's security measures, including encryption and spam protection, to ensure the safety of your communications. By carefully assessing these aspects, you can select an email hosting provider that supports your business's growth and operational needs.
Setting Up Your Business Domain
Once you’ve chosen an email hosting provider, the next step is setting up your business domain. Your domain name is not just a web address; it’s a crucial part of your brand identity. Ideally, your domain should be short, memorable, and reflective of your business name. If you don't already have a domain, you can purchase one through domain registrars like GoDaddy, Namecheap, or directly through your email hosting provider.
After securing your domain, you need to configure it to work with your email hosting service. This typically involves updating the Domain Name System (DNS) settings to point to your email provider’s servers. This step can be a bit technical, but most providers offer detailed guides and support to help you through the process. Proper configuration ensures that the magical and mystical email sending infrastructure properly authenticates you emails allowing them to make it to your business email account and to also reach your recipient.
For all email magic to happen, it is important to set up necessary records, such as SPF, DKIM, and DMARC, to enhance email deliverability and security. These records help prevent your emails from being marked as spam and protect your domain from being used for email spoofing. By carefully setting up your domain, you lay a strong foundation for your business email system, ensuring reliable and secure communication.
What is SPF?
SPF stands for Sender Policy Framework. It’s an email authentication method that helps prevent spammers from sending messages that appear to come from your domain (a practice called spoofing).
At a high level:
- What it does: SPF tells mail servers which IP addresses or hostnames are authorized to send email on behalf of your domain.
- How it works: When a receiving mail server gets an email, it checks the DNS of the sender’s domain for an SPF record. If the sending server’s IP matches what’s in the record, the message passes SPF. If not, it fails.
- How to Configure SPF: You set it up as a DNS TXT record in your domain’s DNS settings (usually managed through your registrar or DNS host, like Cloudflare, GoDaddy, etc.).
- Steps:
- Identify all legitimate mail sources. Your own mail server(s), Third-party services you use to send mail (Mailchimp, Google Workspace, Microsoft 365, etc.), and transactional email providers (like SendGrid, Amazon SES, etc.).
- Write your SPF record. Format:
v=spf1 include:service1.com include:service2.com ip4:x.x.x.x -all
- Example (Google Workspace + Mailchimp):
v=spf1 include:_spf.google.com include:servers.mcsv.net -all
- v=spf1 → Required, says it’s SPF.
- include: → Authorizes third-party services.
- ip4: or ip6: → Lists your server’s IP address(es).
- -all → Fail emails that don’t match. (~all is “soft fail” and more lenient).
- Publish the record.
- Go to your DNS provider.
- Add a record type: TXT
- Host (or Name): @ (this symbol refers to your root domain).
- Value: [your SPF record string]
- TTL (Time To Live) is the number of seconds a record is allowed to be cached by resolvers before they must ask your authoritative DNS again. For TXT records such as SPF/DMARC/DKIM: 900–3600s to start; go longer (14400–86400) once stable.
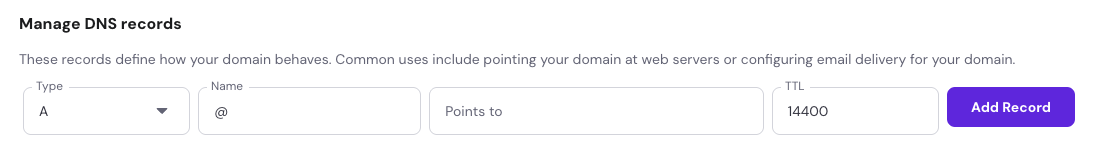
Best practice: Keep only one SPF record per domain. If you need multiple services, combine them into a single record.
What is DKIM?
DKIM stands for Domain Keys Identified Mail. It’s a way to cryptographically sign your emails so receiving servers can verify that:
- The email really came from your domain.
- The content wasn’t altered in transit.
Think of it like a wax seal on a letter — if it’s broken or missing, you know something’s off.
How DKIM Works (Simplified)
When your mail server sends an email, it adds a DKIM-Signature header. This signature is created using a private key that only your sending system has. The receiving mail server looks up the public key in your DNS (published as a TXT record). If the signature matches the public key, the message passes DKIM.
How to Configure DKIM
Configuration depends on your mail provider, but the process is similar everywhere:
- Generate your DKIM key pair. The private key stays with your mail server or service (Google, Microsoft, Mailchimp, SendGrid, etc. usually handle this for you). The public key goes in your DNS as a TXT record.
- Add DKIM TXT record in DNS. The record looks like this:
Host/Name:
selector._domainkey.yourdomain.com
- "selector" is chosen by your provider (e.g., google, s1, k1).
- "_domainkey" is required.
Value (TXT record):
v=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8A...
- v=DKIM1 → DKIM version.
- k=rsa → Key type (RSA).
- p=... → The long public key.
- Enable DKIM in your email platform
- Google Workspace (Gmail):
- Admin Console → Apps → Google Workspace → Gmail → Authenticate Email.
- Choose domain, generate key (1024 or 2048), publish DNS record, then click “Start Authentication.”
- Microsoft 365 / Exchange Online:
- Go to M365 Security & Compliance → DKIM.
- Microsoft gives you 2 CNAMEs to publish in DNS, which point to their hosted DKIM keys.
- Once DNS records propagate, turn on DKIM signing in the portal.
- Other ESPs (SendGrid, Mailchimp, etc.):
- They provide the selector and public key or CNAMEs. You paste those into DNS.
Best Practice:
- Use 2048-bit keys for stronger security (some providers still default to 1024).
- Rotate DKIM keys yearly or if you suspect compromise.
What is DMARC?
DMARC stands for Domain-based Message Authentication, Reporting & Conformance. DMARC is the “traffic cop” that tells receiving mail servers what to do if SPF or DKIM fail.
SPF says: “Here’s who can send mail for me.”
DKIM says: “Here’s how to verify the message isn’t altered.”
DMARC says: “If a message fails SPF or DKIM (and doesn’t align), here’s what to do with it — and send me a report about it.”
Think of it as the policy layer that ties SPF + DKIM together and enforces rules.
Why It Matters
These predefined rules help prevents domain spoofing & phishing, and improves email deliverability & trust. It gives administrators and owners visibility via reports, telling them who’s sending on your behalf).
How to Configure DMARC
- Create a DMARC Record. It’s a TXT record in DNS (similar to SPF/DKIM).
Basic format:
v=DMARC1; p=none; rua=mailto:dmarc-reports@yourdomain.com
- v=DMARC1 → Required version.
- p= → Policy (what to do with failures):
- none = Monitor only (no enforcement, just reports).
- quarantine = Put failing mail in spam/junk.
- reject = Block failing mail.
- rua= → Where to send aggregate reports (XML files, daily summaries).
- ruf= → Where to send forensic/failure reports (optional).
- Example Records
Start in “monitor mode” (safe):
v=DMARC1; p=none; rua=mailto:dmarc@yourdomain.com
Move to quarantine (mild enforcement):
v=DMARC1; p=quarantine; pct=100; rua=mailto:dmarc@yourdomain.com
Full protection (strict):
v=DMARC1; p=reject; pct=100; rua=mailto:dmarc@yourdomain.com
Extra useful tags:
- pct=50 → Apply policy to only 50% of messages (good for testing).
- sp=quarantine → Apply policy to subdomains too.
- adkim=s / aspf=s → Enforce strict alignment (domain must match exactly).
- Publish in DNS
- At your DNS host:
- Type: TXT
- Host/Name: _dmarc
- Value: (your DMARC string).
- Monitor Reports
- Reports are XML files sent by receiving servers.
- Use a DMARC analyzer tool to make them human-readable:
- Postmark DMARC Digests
- DMARCian
- MXToolbox DMARC Analyzer
- EasyDMARC
Best Practice Rollout: Start with p=none to collect reports (2–4 weeks). Fix any legitimate senders failing SPF/DKIM. Once everything appears stable, adjust from "p=none" to "p=quarantine". Finally, go to "p=reject" for maximum protection.
Test your records
Once configured you can use tools such as MXToolbox to check your configuration. You can also get instructions for grabbing headers from your emails and test those for passing or failing on all three record types:
Creating Your Personal Business Email Account
With your domain set up, the next step is to create your business email account. This involves setting up your email addresses for yourself, and it’s a good idea to establish naming conventions for email addresses to maintain consistency. For instance, using first.last@yourdomain.com or firstname@yourdomain.com can help keep your email addresses organized and easy to remember.
Creating email individual email accounts is straightforward with most email hosting providers. You’ll need to log in to your admin panel and follow the prompts to add new users. During this process, you can assign roles and permissions, ensuring that each team member has the appropriate level of access.
By thoughtfully setting up your business email accounts, you create a professional and efficient communication system that supports your team’s needs.
Configuring Email Clients and Applications
After creating your business email accounts, the next step is configuring email clients and applications to access your emails. Most professionals use email clients like Microsoft Outlook, Apple Mail, or web-based clients provided by their email hosting service. These clients offer various features that can enhance your email experience, such as calendar integration, task management, and contact organization.
To configure your email client, you’ll need your email account details, including the incoming and outgoing server settings provided by your email host. This information is usually available in the help or support section of your email hosting provider’s website. Once you have these details, you can enter them into your email client’s settings to set up your account. This process typically involves selecting the account type (IMAP or POP3), entering your server information, and authenticating your account with your email address and password.
Additionally, consider setting up your email on mobile devices to ensure you can access your business emails on the go. Most email hosting providers offer mobile apps or compatibility with built-in email apps on iOS and Android devices. By configuring your email clients and applications, you ensure seamless access to your business emails, allowing you to stay connected and productive wherever you are.
Essential Features of a Business Email
A professional business email is equipped with essential features that go beyond basic email sending and receiving. These features are designed to enhance productivity, collaboration, and security. One crucial feature is the ability to create custom email aliases, shared mailboxes, and distribution lists. Email aliases allow you to create multiple email addresses that forward to a single inbox, making it easier to manage different types of inquiries. Shared mailboxes are owned by the org, and accessible by multiple users with delegated permissions. These are good for teams that need to read, reply, and manage messages from the same inbox, with shared visibility and maintain continuity when staff changes. Distribution lists enable you to send emails to a group of people with a single address, streamlining team communication.
Another important feature is calendar integration. Many business email services offer built-in calendars that sync with your email account, allowing you to schedule meetings, set reminders, and manage your time effectively. This integration helps ensure that you never miss an important appointment or deadline, and it enhances collaboration by allowing team members to share their availability and schedule meetings effortlessly.
Security features are also paramount for business emails. Look for services that offer robust spam filters, virus protection, and encryption to safeguard your communications. Two-factor authentication (2FA) is another valuable security feature, providing an extra layer of protection by requiring a second form of verification in addition to your password. By leveraging these essential features, you can optimize your business email for efficiency, collaboration, and security.
Best Practices for Email Management
Effective email management is crucial for maintaining productivity and ensuring that important communications are not overlooked. One of the best practices is to establish a regular routine for checking and responding to emails. Set specific times during the day to review your inbox, rather than constantly checking emails, which can disrupt your workflow. This approach helps you stay focused on your tasks while ensuring that you respond to emails in a timely manner.
Organizing your inbox is another key aspect of email management. Use folders, labels, and filters to categorize your emails based on their importance and relevance. For example, you might create folders for client communications, internal team emails, and newsletters. Filters can automatically sort incoming emails into the appropriate folders, reducing clutter in your main inbox. By keeping your inbox organized, you can quickly locate important emails and keep track of ongoing conversations.
Another best practice is to use clear and concise subject lines and email content. This helps recipients understand the purpose of your email at a glance and makes it easier for them to prioritize their responses. Additionally, avoid using jargon or overly complex language, as this can lead to misunderstandings. By following these best practices, you can enhance your email management, ensuring efficient and effective communication with clients and colleagues.
Email Security Tips for Businesses
Email security is a critical concern for businesses, as email accounts are often targeted by cybercriminals seeking to steal sensitive information. One of the most effective ways to enhance email security is to implement strong, unique passwords for each email account. Avoid using easily guessable passwords or reusing passwords across multiple accounts. Instead, use a combination of letters, numbers, and special characters to create robust passwords, and consider using a password manager to keep track of them.
Another important security measure is to enable two-factor authentication (2FA) for your email accounts. 2FA adds an extra layer of protection by requiring a second form of verification, such as a code sent to your mobile device, in addition to your password. This makes it significantly harder for unauthorized users to access your accounts, even if they manage to obtain your password.
Regularly updating your software and email clients is also crucial for maintaining security. Software updates often include patches for security vulnerabilities, so keeping your systems up to date can help protect against potential threats. Additionally, educate your team about common email security risks, such as phishing attacks and malware, and encourage them to be cautious when opening attachments or clicking on links from unknown sources. By implementing these email security tips, you can safeguard your business communications and protect sensitive information.
Common Mistakes to Avoid When Setting Up Your Email
Setting up a business email involves several steps, and it's easy to make mistakes that can impact your email's functionality and security. One common mistake is choosing an inappropriate email hosting provider without thoroughly researching your options. Selecting a provider based solely on cost or convenience can lead to issues such as insufficient storage, lack of essential features, or poor customer support. Take the time to evaluate different providers and choose one that aligns with your business needs.
Another mistake is neglecting to configure your domain settings correctly. Incorrect DNS settings can result in emails not being delivered or being marked as spam. Ensure that you follow your email hosting provider’s instructions carefully when setting up your domain, and verify that all necessary records, such as SPF, DKIM, and DMARC, are properly configured. These records help improve email deliverability and protect against email spoofing.
Failing to implement adequate security measures is another common oversight. Without strong passwords, two-factor authentication, and regular software updates, your email accounts are vulnerable to cyberattacks. Additionally, not educating your team about email security best practices can increase the risk of phishing and other threats. By avoiding these common mistakes, you can ensure a smooth and secure setup for your business email.
Conclusion: Elevating Your Business Communication
Setting up a professional business email is a vital step in enhancing your brand's professionalism and productivity. By following this step-by-step guide, you can create an email system that supports your business's unique needs and helps you make a lasting impression on clients and colleagues. From choosing the right email hosting provider to implementing essential security measures, each step is crucial in building a robust and efficient communication infrastructure.
A professional business email not only boosts your credibility but also streamlines your communication processes, allowing you to focus on what matters most—growing your business. By leveraging the features and best practices discussed in this guide, you can optimize your email management, enhance collaboration, and protect your sensitive information from cyber threats.
As you implement these steps, remember that your business email is more than just a tool; it's a reflection of your brand. Take the time to set it up correctly and maintain it diligently, and you'll reap the benefits of improved professionalism and productivity in your business communications.